Some mini writeups on Codegate 2011 Prequals: Issue100,200, Net100,200, Crypto100,200.
Issue 100
The image is a factor in the black box of the car.
There was a car crash at the final destination.
Where the “spot” exactly did happen? (Except country)
If we do strings on this file, we can notice pairs of numbers looking like:
NE3736.0265
12700.0994
It seems that they are coordinates! Let’s look what is at the last coordinate:
hellman $ strings task.asf | grep -E -A1 'NE[0-9]{1,4}\.' | tail -n 2 NE3736.1213 12659.8566
Then just look at google maps 37 36.1213 126 59.8566 and get the address.
The flag: San 15-3 Seongbuk-dong, Seongbuk-gu, Seoul
Issue 200
We were given a file and a text like “can you read the message?”.
If we look at contents of the file, we can think that it is encrypted. Let’s try my tool xortool to check if it’s xored. Also, probably it is an image – binary data – so the most frequent char should be \x00. So let’s run it:
hellman $ xortool -c 00 task Probable key lengths: 2: 6.2 % 4: 9.8 % 6: 6.2 % 8: 9.4 % 10: 6.3 % 12: 9.2 % 14: 6.2 % 16: 8.7 % 20: 8.1 % 22: 6.5 % 24: 8.7 % 26: 6.5 % 28: 8.5 % Key-length should be 4*n Probable keys: ['CODE']
Wow, looks like it’s really xor-encoded (guessed key makes a sense). Then, what is the decrypted file?
hellman $ file xortool/00_CODE xortool/00_CODE: PNG image, 256 x 64, 8-bit colormap, non-interlaced
Image, hehe:
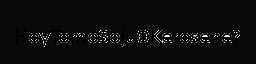
Finally, fill it with gray:
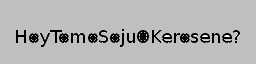
The flag: HoyTomoSojuOKerosene?
Network 100
Here a pcap file was given and we need to find md5sum of malicious file.
Wireshark has a nice feature (File - Export - Objects - HTTP) – viewing and extracting downloaded via HTTP files. Quick look through them – and we see the only exe file – H1A1.exe, which seems to be malicious. Get the md5 and we win.
The flag: 7A5807A5144369965223903CB643C60E
hey, you stole my writeup! :D — vos
Network 200
This task is also a pcap file.
For a long time no teams could solve it, and some hints were given:
– there is a hidden channel
– information is encrypted with XOR, the key is some human readable data from the packet
The traffic consists of some CUPS packets, pings and NBNS packets. It’s easy to notice strange payload in ping packets:
Packet #2
0030 00 00 00 00 02 00 00 00 00 00 00 00 69 64 0a ........ ....id.
Packet #10
0030 00 00 00 00 02 00 00 00 00 00 00 00 52 53 43 0e ........ ....RSC.
0040 1f 7b 43 4b 43 42 1d 59 1e 56 4f 44 4b 1e 42 5d .{CKCB.Y .VODK.B]
0050 5b 58 1e 5a 48 5a 3b [X.ZHZ;
Packet #11
0030 00 00 00 00 00 00 00 00 00 00 00 00 5a 57 4e 14 ........ ....ZWN.
0040 10 4d 00 58 02 43 46 54 46 51 40 5e 4b 5d 54 4a .M.X.CFT FQ@^K]TJ
0050 03 43 40 42 55 24 .C@BU$ Don’t know how it can be guessed, but the key for xoring them is 127.0.0.1:
hellman $ xor -f stripped_packet_10 -s "127.0.0.1" cat /Users/n0fate/solv.txt hellman $ xor -f stripped_packet_11 -s "127.0.0.1" key: c0v3rtchannelex4mple
The flag: c0v3rtchannelex4mple
Crypto 100
An image with numbers like 444 66 222 777 999... was given. Easy to guess, these are letters from mobile phones – 4 pressed 3 time, 6 pressed 2 times, etc. Decode:
#!/usr/bin/env python #-*- coding:utf-8 -*- import sys alpha = ".,-?abc~def~ghi~jkl~mno~pqrstuv~wxyz" s = open("numbers.txt").read().strip() for num in s.split(): a = (int(num) % 10) - 1 b = len(num)-1 sys.stdout.write(alpha[a*4 + b]) print
hellman $ python test.py incryptographyasubstitutioncipherisamethodofencryptionbywhichunitsofplaintextare replacedwithciphertextaccordingtoaregularsystemtheunitsmaybesingleletterspairsof letterstripletsoflettersmixturesoftheabovethisciphertextisencryptedbytelephoneke ypadsowecallthiskeypadcipher
Add spaces:
In cryptography a substitution cipher is a method of encryption by which units of plaintext are replaced with ciphertext according to a regular system. The units may be single letters, pairs of letters, triplets of letters, mixtures of the above. This ciphertext is encrypted by telephone keypad so we call this keypad cipher.
The flag: KEYPAD CIPHER
hey you again stolen my writeup >: / — vos
Crypto 200
A text file was given. If the first crypto was just a monoalphabetic substitution cipher, then the second should be the polyalphabetic. The most well-known one is Vigenere cipher, so let’s try to crack it. I used CrypTool here:
Analysis -> Symmetric Encryption (classic) -> Ciphertext-only -> Vigenere
It says that key is KRIPTOKRIPWOKRIJTO:
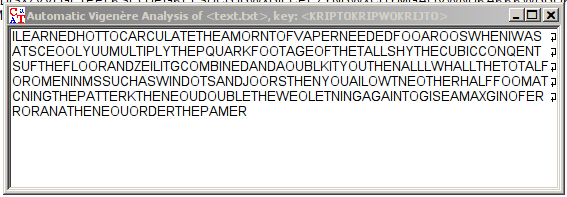
Looks like it’s a small probabilistic mistake, and the real key is KRIPTO:
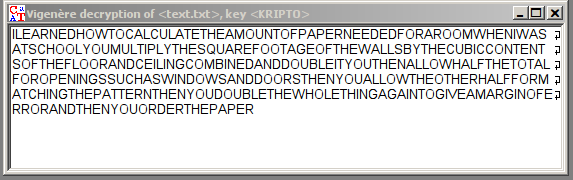
But, there’s no flags in the text, so it’s the encryption key itself.
The flag: KRIPTO
