What is the password?
Category: packets
Hint: TeLaViv is a packet forensics challenge.
file
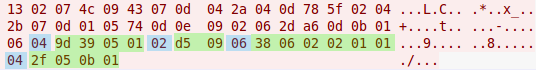
This is a traffic dump file, with only one stream:
Easy to guess, the password is encoded somewhere after "Gits\0Plague\0".
If you look attentively at the data, you’ll notice a pattern: a number, a piece of that length; a number; a piece of that length…
It’s important, that if you separate the data, you’ll use all the bytes and no one will be left – this means we are on the right way.
So, there are 37 blocks:
8 '+.\x01\x17\x10\x01\x05\x01'
7 'W!W\x01\x01\x12\x01'
6 'M]\x1d\x08\r\x02'
5 '\x1b\n\x18\x02\x01'
4 'Z\x04F\x10'
5 "\x84'\x16\x12\x03"
5 '\x9d"\x05\x01\x01'
4 '\xb8\t\x04\x01'
5 '3]8\x05\x01'
4 '^\rh\x1f'
...
What we should do with that?
The number of blocks – 37 is likely to be a length of the password (else it will be too long). So, it’s rather that one block represents one symbol.
We can try to xor all bytes in each block together, but the right way is adding them.
After summing bytes in each block we get:
0000000: 88e4 de40 b4d6 c6c6 cef2 c4dc 40e6 c674 ...@........@..t
0000010: 4044 88e4 de40 9cd6 408c e6f0 dae6 409a @D...@..@.....@.
0000020: f2dc de44 40
The most frequent char is 0x40 – but it should be space (0x20). So, let’s try to shift it right with one bit:
#!/usr/bin/env python #-*- coding:utf-8 -*- from scapy.all import * ps = rdpcap("task1.pcap") s = str(ps[5]['Raw'])[12:] res = "" while s: size = ord(s[0]) text = s[1:1+size] res += chr(sum(map(ord, text))>>1) s = s[1+size:] print res |
Run it and you get Dro Zkccgybn sc: "Dro Nk Fsxms Myno".
Obviously, do rot16 and
The Password is: “The Da Vinci Code”