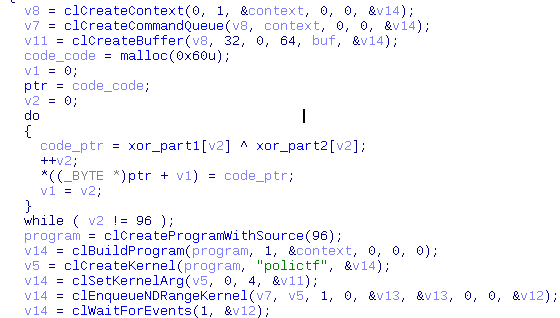
This is an OpenCL binary. Go!
Summary: xor and xor
This challenge was very easy:
We see some code is xored, and the argument to the code is:
Dexor code:
$ dd if=opencl bs=1 skip=$(rax2 0x11c0) count=98 of=part1 98+0 records in 98+0 records out 98 bytes (98 B) copied, 0.00108629 s, 90.2 kB/s $ dd if=opencl bs=1 skip=$(rax2 0xdd1) count=98 of=part2 98+0 records in 98+0 records out 98 bytes (98 B) copied, 0.00106548 s, 92.0 kB/s $ xor -f part1 -f part2 __kernel void polictf(__global char *a){int i=get_global_id(0);__local char f[64];f[i]=i^a[i];} |
Oh, it simply xors each char in argument with it’s index:
In [1]: "".join([chr(ord(c) ^ i) for i, c in enumerate("dd`vcZiwmgigSdzPybMrKgsvtFjzusAvN~VKAzGT[)")]) Out[1]: 'debug_opencl_it_is_a_real_pain_in_the_ass\x00' |
The flag: debug_opencl_it_is_a_real_pain_in_the_ass
PS: There was very similar challenge on Hacklu CTF 2012 – just CUDA instead of OpenCL and one more additional xor in it’s logic